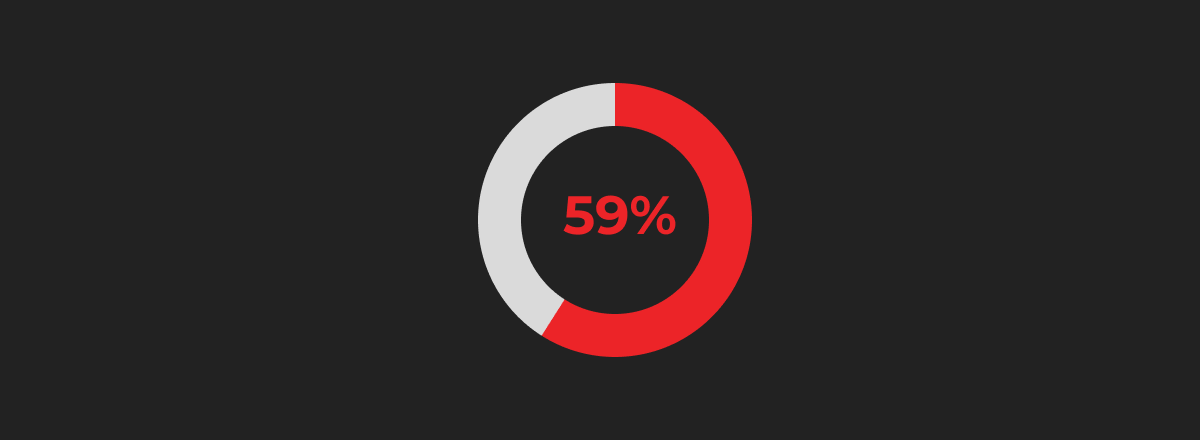
As more Australian businesses move toward the cloud, securing digital assets is more necessary than ever. According to Australian Cyber Security Magazine, 59% of Australian organisations already use cloud services—many on AWS. As adoption grows, so too does the risk of misconfiguration, data breaches, and compliance failures.
Having AWS security experts on hand means your assets are well-protected and compliant with all regulatory standards. This guide outlines 14 key considerations to help you choose the right partner and strengthen your business’s cloud security posture.
Australian businesses using cloud technology (as of January 2024):
Source: Australian Cyber Security Magazine
1. Certification and Specialisation
Ensure the experts hold the AWS Certified Security Speciality certification, which validates their ability to secure AWS workloads and architectures. This certification demonstrates proficiency in data protection, incident response, and security operations within AWS environments.
2. Security Incident Response Capability
Professionals should follow AWS Security Incident Response best practices using AWS-native or third-party tools to manage and contain threats. They must also have hands-on experience in forensic investigations, including log analysis, root cause identification, and secure recovery.
Key capabilities include:
- Applying a structured incident response model
- Investigating incidents through log and evidence analysis
- Supporting secure remediation with maximum speed and minimal disruption
3. Understanding of the Shared Responsibility Model
Experts must clearly articulate AWS’s shared responsibility model to avoid confusion around who is accountable for what. While AWS secures the infrastructure, you are responsible for securing your data, configurations, and applications. This clarity ensures all parties are aligned and nothing slips through the cracks.
What they’ll do:
- Define which responsibilities AWS handles (e.g. physical infrastructure, network, hypervisor security)
- Identify the controls you are responsible for (e.g. access policies, application logic, data security)
- Recommend governance frameworks to ensure your internal security aligns with AWS’s shared responsibility model
4. Mastery of Identity Best Practices
Implementing least-privilege access, strong credential management, and regular audits is fundamental. Experts should be proficient in AWS Identity and Access Management (IAM) to enforce strict access controls and enable the ability to monitor user activities effectively.
5. Visibility and Logging Strategies
From the outset, AWS CloudTrail, AWS Config, Amazon GuardDuty, and other logging tools should be configured to ensure comprehensive visibility into your AWS environment. These tools facilitate continuous monitoring and help identify and respond to security threats quickly.
6. Automation of Compliance and Risk Management
AWS security experts will implement automation using AWS Config, AWS Security Hub, and custom AWS Lambda functions to enforce compliance and manage risk at scale. Automation ensures policies are applied consistently and non-compliant resources are identified and addressed quickly.
7. Secure CI/CD Pipeline Expertise
Experts will secure application pipelines using automated vulnerability scans. Integrating security into the CI/CD process ensures that applications and configurations are tested for vulnerabilities before deployment, reducing the risk of introducing security flaws into your organisation’s production environments.
8. Familiarity with Multi-Account Security Architecture
A robust multi-account security strategy is essential for organisations operating at scale in AWS. By structuring your environment with distinct accounts for different workloads or business units, you improve isolation, limit the impact of breaches, and simplify governance.
What your AWS security expert will do:
- Design and implement a multi-account architecture tailored to your operational and security needs
- Enforce guardrails using AWS Organisations and Service Control Policies (SCPs) to restrict unsafe actions
- Configure cross-account IAM roles for secure and auditable access between environments
- Align account structure with compliance and audit requirements for better visibility and control
9. Continuous Threat Detection Capabilities
AWS security experts will configure and manage continuous threat detection using services like Amazon GuardDuty and AWS Inspector, along with integrated third-party tools. They will monitor for real-time anomalies and respond swiftly to emerging threats to minimise risk and impact.
10. Integration with Existing SIEM/SOAR Tools
Ensure that the experts can integrate AWS logs with your enterprise SIEM (Security Information and Event Management) or SOAR (Security Orchestration, Automation, and Response) tools. This integration facilitates centralised monitoring and streamlined incident response processes.
11. Application and Web Security Proficiency
AWS Web Application Firewall (WAF), AWS Shield, certificate management, and runtime protection are essential to protect your organisation’s web applications. These measures protect against common web exploits and ensure the integrity and availability of your applications.
Having an AWS security expert who can also run penetration testing against your application services is a value add that should not be ignored lightly.
12. Knowledge of Data Protection Mechanisms
An accredited AWS security expert will deploy AWS-native protections such as AWS WAF, AWS Shield, and runtime security tools, like Amazon GuardDuty, to protect your APIs and web applications from common threats like DDoS attacks and zero-day exploits. They’ll also implement at rest and in transit encryption, applying AWS KMS best practices, and set granular bucket-level access controls. Together, these controls form a multi-layered defence against modern cloud threats.
13. Proactive Security Posture and Roadmap Planning
A strong AWS security posture requires ongoing review and adaptation, not a set-and-forget approach. Experts should conduct regular assessments, tests, and red-team exercises to identify and address gaps early. Findings should shape a security roadmap that evolves with your risk profile.
This proactive approach keeps you ahead of emerging threats with:
- Risk-aligned security maturity planning
- Prioritised controls based on real threats
- Scalable strategies as your cloud environment grows
- Continuous posture reviews using AWS tools and intelligence
14. Experience in Remediation of AWS Security Environments
Even well-managed AWS environments can face misconfigurations or vulnerabilities. Skilled security experts must quickly identify issues, assess their impact, and resolve them without disrupting services.
Remediation requires a firm grasp of AWS tools and safe change practices. A capable expert should:
- Triage risks using AWS-native monitoring and logs
- Resolve IAM, resource, or data exposure issues securely
- Apply fixes with minimal disruption to operations
- Maintain clear documentation for audits and compliance
Conclusion
As more Australian organisations move to the cloud, securing AWS environments is critical. The right AWS security expert offers strategic insight and hands-on capability, managing responsibilities, securing pipelines, and enabling real-time threat detection. Whether starting fresh or improving existing infrastructure, these insights support a secure, scalable cloud environment that aligns with your business goals.
RedBear are the AWS Security Experts For the Job
RedBear offers comprehensive AWS security services tailored to your organisation’s unique needs. Our team of certified professionals is ready to assist you in enhancing your AWS security framework.
Visit our Security Incident Response page to learn how we can help secure your business.