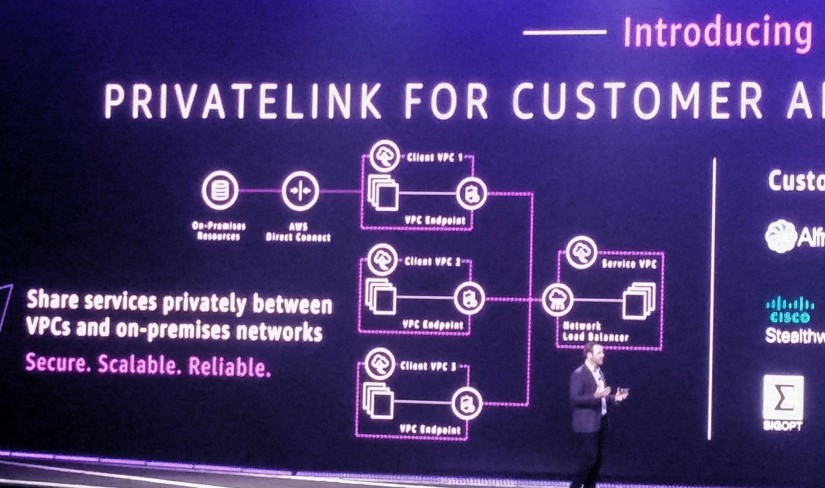
re:Inforce 2019 – wrap up
The debut running of the AWS security conference re:Inforce 2019 has wrapped up in Boston today. RedBear were on the ground to soak…
Security as an enabler for business
Traditionally, security has been seen as a guardian against change. It has been thought of as a silo. It's a box you need…
Multi-cloud – is it what we thought?
Early ideals in multi-cloud In the early days of Cloud, there was much talk of a multi-cloud approach. As the number of public…