Last week the Australian government announced that government services had been under a sustained cyber attack. They said it had been happening for a while and had the footprint of a nation state level attack. No breaches were revealed.

Don’t cyber attacks happen all the time?
Well, yes, but this one was different. The key was the scale of the attack. It was across industries, including critical infrastructure such as health. The attack was also targeted at Australia. As a result of the scale, your organisation may have been targeted? Also, with no breaches reported, it may mean that low levels of so far undetected compromise have occurred.
What does this mean for your organisation? In order to reduce your risk, here are five basic mitigations that you should adopt (if you aren’t already!).
1 – Anti-phishing education
Phishing (or the targeted spear-phishing variant) is the most common method of cyber attack, usually via email. The attacker will include links to fake sites to harvest credentials. Alternatively, they may include attachments, such as a Powerpoint presentation, with malicious content.
Either way, it is important to educate your teams on how to spot such phishing campaigns. You should have a way for your teams to report on such emails. Your email service provider, such as Office 365, will most likely have anti-phishing tooling available which you should enable. While you are at it, block the use of macros in Office applications.
There are some excellent free anti-phishing tools and training out there, such as Phish Insight offered by Trend Micro.
2 – Multi-factor authentication
One of the easiest ways to reduce the risk of your organisation to a cyber attack is through the use of multi-factor authentication (MFA). MFA is a solution where access to a service requires a password and another “factor” such as a code from an identity application or one sent via SMS.
Assuming that you centralise your identity (and you should!), enabling it can managed through a single solution. However, it can be difficult to rapidly implement company wide. First focus on remote access (likely a common pattern in post COVID-19 times) and elevated access, such as administration level access.
3 – Patching
One of the easiest ways to reduce risk and exposure to compromise is to keep your systems up to date. This applies to both applications and operating systems. In the ACSC briefing on the cyber attack, they particularly focussed on targeted attacks against known vulnerabilities in Citrix ADC, Sharepoint, Telerik UI and IIS. Recent data from TrendMicro identified 709 vulnerable Citrix server on the Internet in Australia! Patches and mitigations are available for these vulnerabilities.
Implementing a good patching strategy is crucial to reduce risk to your environments. Traditional environments can struggle to implement patches in a timely manner. In AWS Cloud based environments, automated patching is easy to implement, particularly for environments provisioned through code. It’s easy to launch a new instance, patch it and the rotate it into production. The new instance becomes the golden image for any future launches until the next round of patching. Adopting a SaaS solution means that the service provider takes care of patching and currency of the environments.
Another reason why you can be more secure in the Cloud.
4 – Vulnerability Management
Knowing your exposure to vulnerabilities allows you to focus your efforts. With a long list of vulnerabilities and a large environment, it can become impossible to stay on top of closing potential holes.
A good vulnerability management solution, such as Rapid7’s InsightVM, will take into account how exploitable the vulnerability is. It also allows you to enrich assets with information such as where it is in the network, data sensitivity and the criticality of the related applications so you can focus your resources on mitigating the key exposures.
You can also apply vulnerability assessments to your overall infrastructure. That may be through programs such as the AWS Well Architected Review or an assessment against security benchmarks, such as CIS or the ASD Essential 8. It may also be through penetration testing of applications and services.
5 – Visibility of cyber attacks
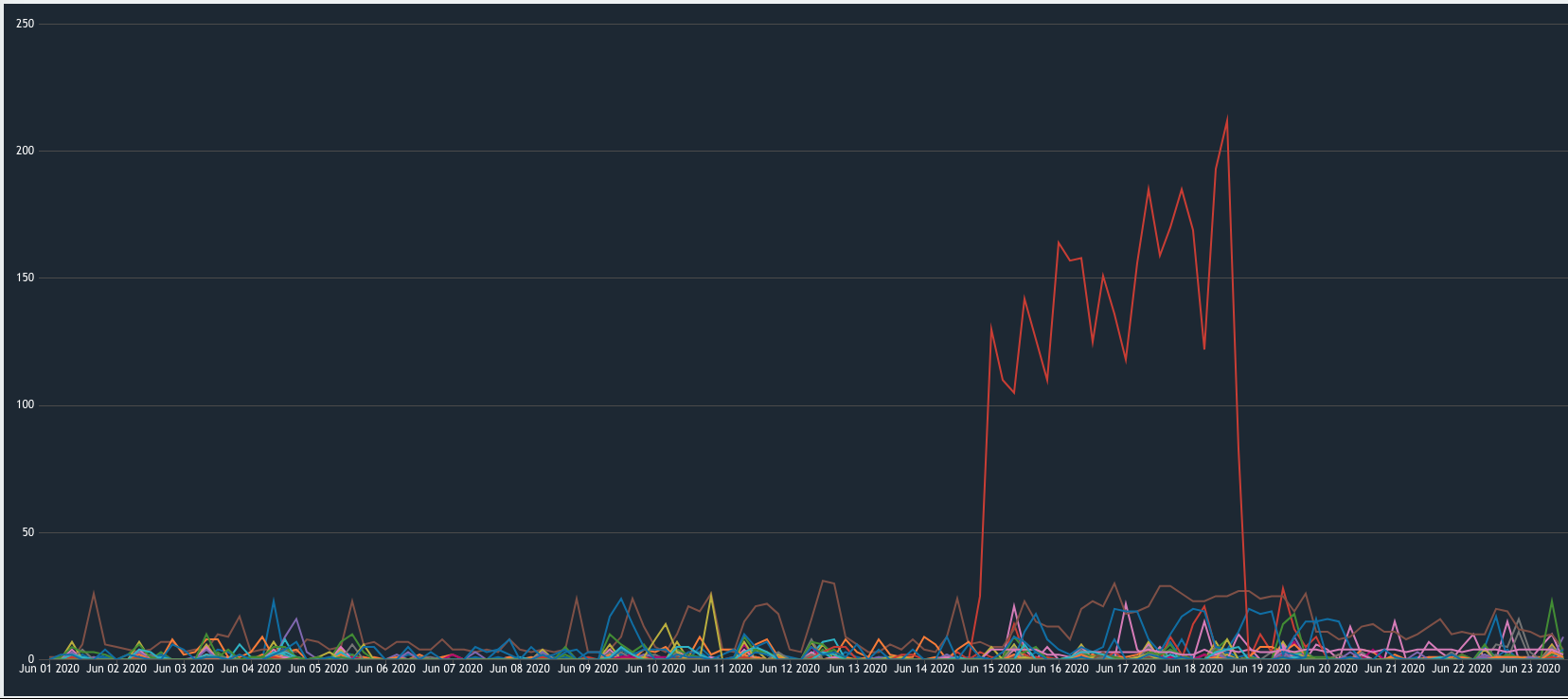
If you can’t see the activity in your environment, how can you secure it? Detect and respond depends on having the insight into your environment. Here’s some data from our cloud security managed services platforms for our customers. The spike you can see is the amount of blocked malicious IPs that our platform automatically remediated. That’s a definite correlation with the government’s announcement from last week!
Today’s system can generate a lot of data and it is impossible to manually deal with that. How do you filter all the data to find the meaningful and actionable alerts? How do you automatically pickup configuration changes or service updates to your environments? Visibility is a keep step in securing your environments. A visibility tool, such as Sumologic, will allow you to ingest and process data to generate dashboards and alerts. It also gives you an out-of-band audit trail that you can use for forensics should suspicious activity occur.
Where next?
Once you have visibility, you can look at more advanced capability such as automation for discovery and response. Another advantage of AWS Cloud environments is the ability to quickly implement automation. You can use the built in APIs to discover new services or EC2 instances and automatically add them to monitoring. Similarly, you can use the same APIs to close down malicious activity in seconds.
Speak to us if you want an assessment of your current risk exposure or if you are looking for some help with these measures. Even if you want to understand more about the cyber attack from the government announcement last week, we are here to help!