In this bonus blog of our AWS Security Foundation series, we focus on the AWS Backup service. You might ask why we put backups as a capability to think about under security? Read on to find out more!
Background
AWS Backup has been available as a service for a number of years. Recently, the service added the native capability of copying backup images to a secondary account and/or region. At RedBear we have been providing this capability for our customers using a hand crafted solution. Now, we can go native!
Having the ability to protect your backups is a key solution to protect against ransomware. 2020 saw the greatest number of ransomware attacks in a single year. Sadly, it’s not just large enterprises with deep pockets that are the target. Even small companies can fall victim.
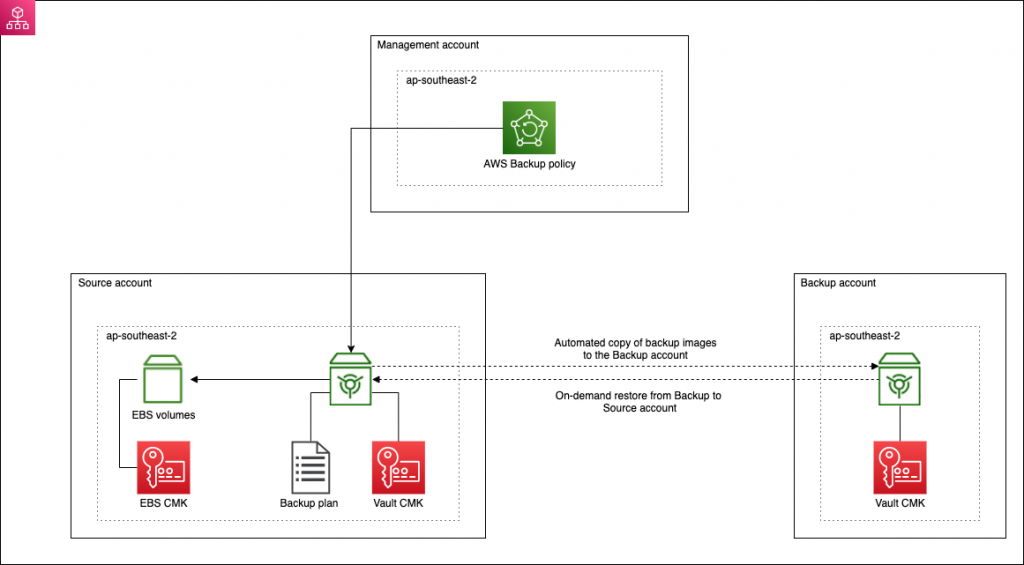
The ideal solution is to be able to seamless copy backup images into an account where the image is then encrypted with a new key. This removes dependency on the local source account. The Backup account should also have a different set of credentials to the source account(s). Should the source account be compromised, the malicious actor should not be able to delete, override or render unusable the backup images or have any access to the Backup account.
AWS Backup requirements
In order to implement this kind of solution using AWS Backup, the following requirements apply.
- You need a multi-account setup that uses AWS Organizations. Unfortunately, all the configuration of AWS Backup needs to be done from the Organization Management (master) account. There’s no concept of a delegated master account like there is for other services;
- Create a dedicated Backup account;
- Each source account requires a vault with a customer managed CMK;
- The Backup account requires a vault with a customer managed CMK;
- If you are encrypting your EBS volumes (of course you are!), you need to ensure that it is using a customer managed CMK;
- You will need an IAM role in all accounts where you plan to use AWS Backup. This role is used by AWS Backup to perform the backup and then copy it to the Backup account.
Getting started
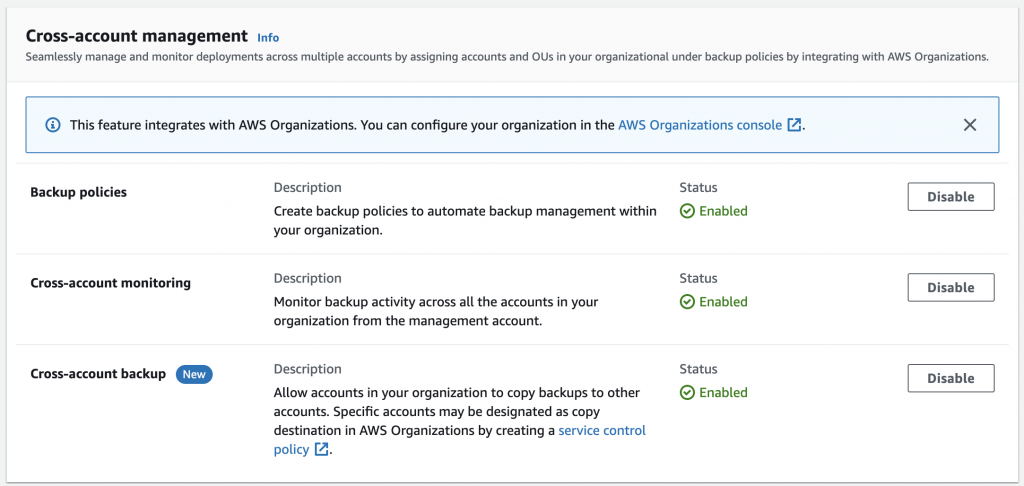
The first thing to do is to go into the AWS Backup console in the Organization Administrator account and enable all features Organization wide.
Create vaults and roles
In each account:
- Create a new role for AWS Backup. Use the following AWS managed policies:
AWSBackupServiceRolePolicyForBackup AWSBackupServiceRolePolicyForRestores
- Allow the AWS Backup service to assume the role as a trusted entity;
- Create a new vault using a customer managed CMK. In the key policy, allow all users of the local account to make use of the CMK.
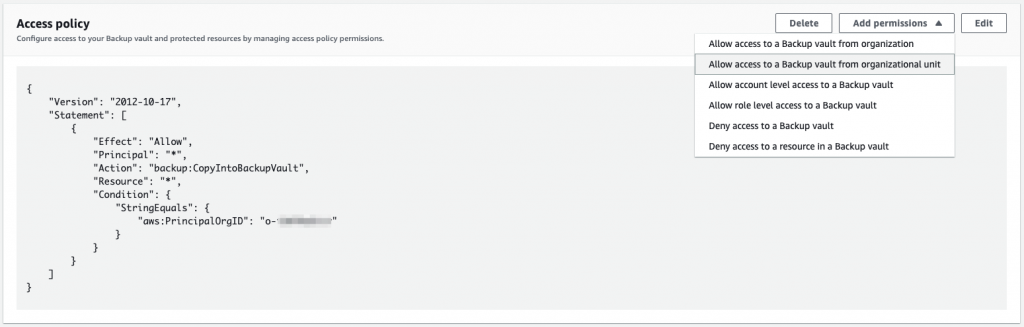
In the backup account, allow other accounts in the Organization to copy into the Backup account vault via the access policy.
If you want the Backup account to be able to restore back to a source account, then the Backup account will also need permission in the source account vault access policy.
Providing key access
In order to allow the replication to work, the Backup account will need the ability to use the KMS CMKs for both the source vault and for the EBS key used for encryption in the source account. This is done through the key policy.
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<backup_account_id>:root"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<backup_account_id>:root"
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}
If you haven’t setup EC2 encryption to use a customer managed CMK, now is the time to do so!
All source accounts will also need the ability to use the CMK configured for the Backup vault.
Setting up a backup policy
To enable cross-account replication, you need to setup a backup policy. This is done from the Organization Management account. Note that you can have multiple policies and apply them to different accounts. You can even apply multiple policies to an account with different configurations for each policy for different resources (the policy will be applied based on the tags configured for that policy).
- From the AWS Backup console, go to the My organization section, select Backup policies and click on Create backup policy;
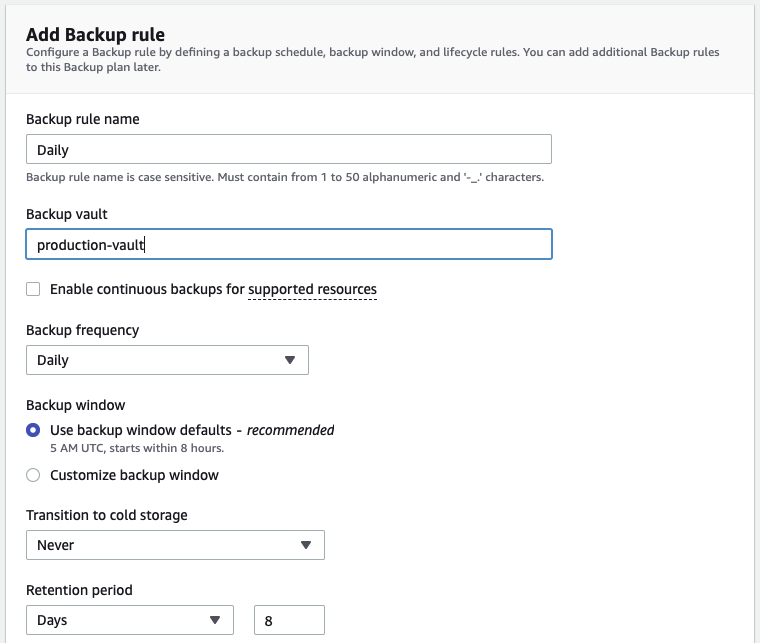
- Configure the backup plan to use the appropriate region, generally only ap-southeast-2 for our customers;
- Create a Backup rule providing the frequency, backup window and retention;
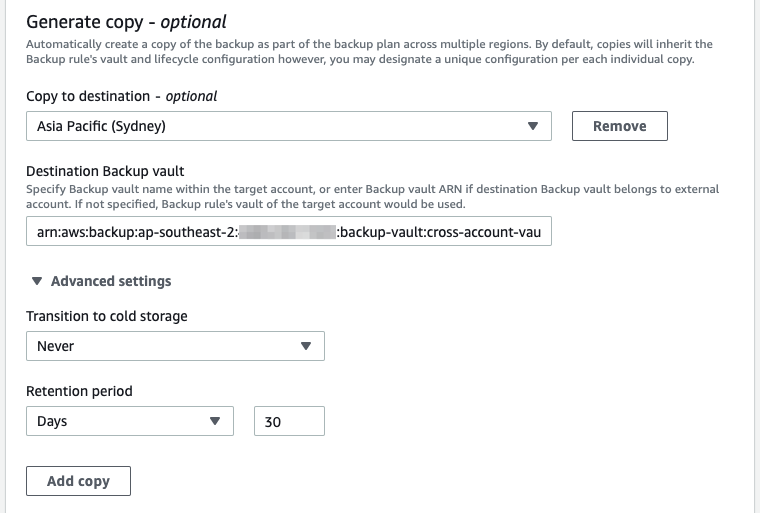
- Under the Generate copy section, add the destination region, the ARN of the vault in the Backup account and the retention period for the copy;
- Add a Backup rule for each backup type (daily, weekly etc.);
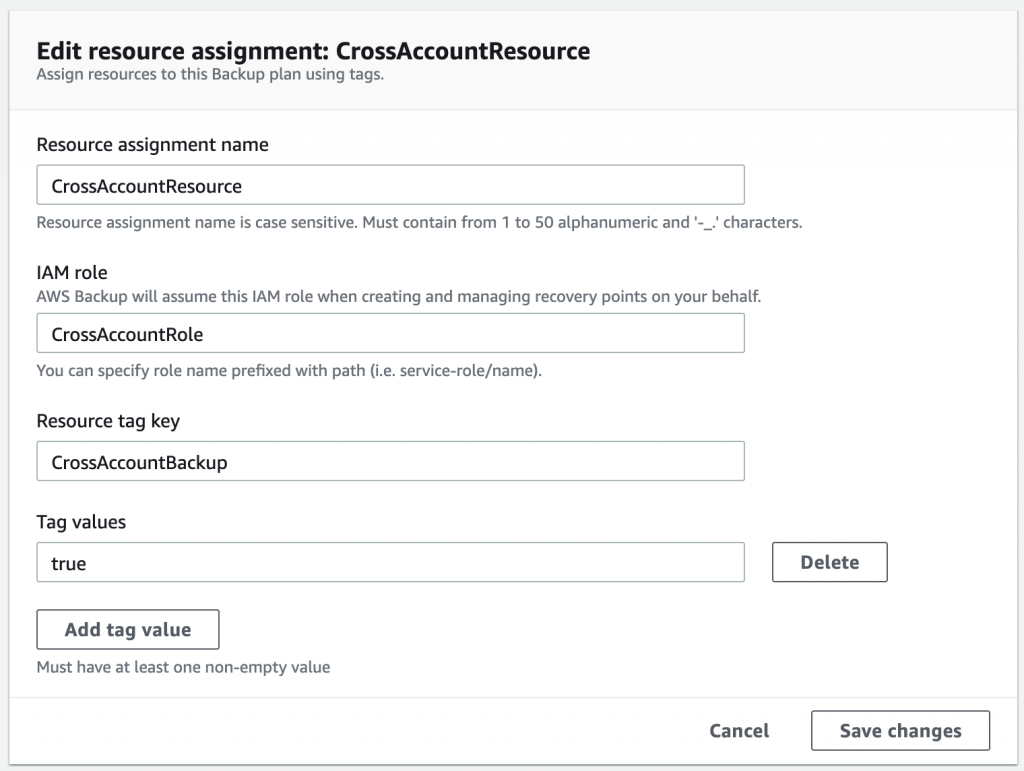
- Under the Assign resources section, add the role details. Use the role name that was created earlier;
- Define a Resource tag key. This tag key and value is used to identify resources (such as EC2 instances) that will be backed up using this policy and the backup image copied to the Backup account;
- Once you have created the policy, the final step is to select the account(s) to which to apply the policy.
Testing
We are now ready to give it a go!
In order to test the back and replication, modify the backup window to start within the next few minutes. Note that the backup window is in UTC not localtime! Pro Tip – always set the Start within configuration to the minimum of 1 hour to speed up this testing.
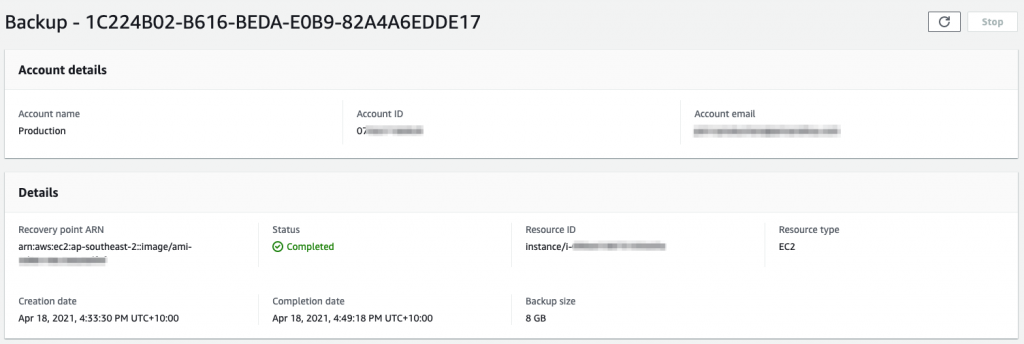
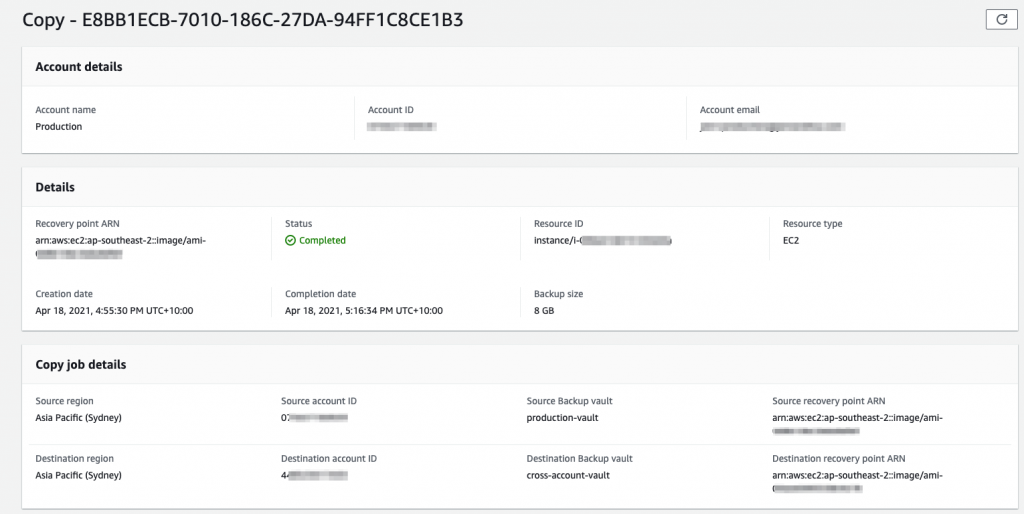
Keep an eye on the Cross-account monitoring to see the job under the Backup jobs tab. Once it has completed successfully, you will shortly see the copy operation under the Copy jobs tab. Once that has completed, hop into the Backup account and you will see Protected resources showing the source account.
You can also test an on-demand restore.
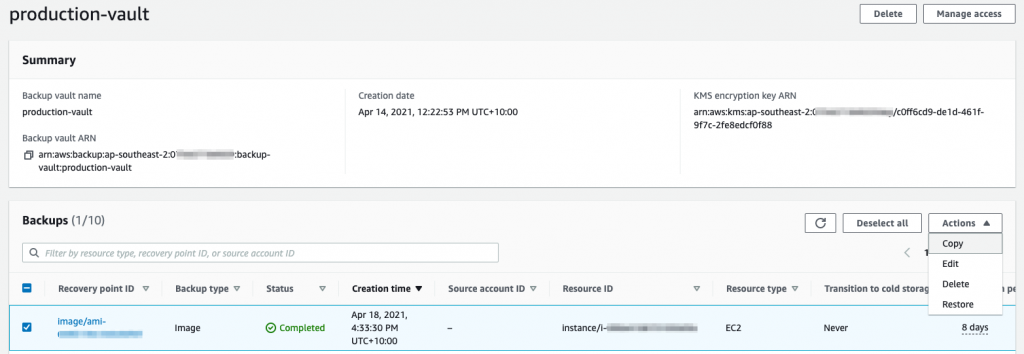
- From the Backup account, select a backup under vault;
- Select Copy from the Actions drop down;
- From here, you will be able to copy the backup back to the source account. Don’t forget to add the role created earlier for this copy operation;
- Once it is copied backup, you can Restore the resource from the source account.
Troubleshooting
If you have problems, CloudTrail is your friend. You will need to look at the source account and backup account to determine the issue. The most likely culprit is permissions for roles to access KMS keys!
You can re-test by creating an on-demand copy once you have a successful backup in a source account.
- Go the vault in the source account;
- Select a backup and then select Copy from the Actions drop down;
- You then provide the Backup vault and the role details (matching the policy) to test the copy process. Make sure you select Copy to another account’s vault to test the configuration.
Wrapping up
There’s a bit of back and forth and configuration required in setting up a robust multi-account backup solution. However, it does achieve the goal of allowing you to centrally manage and protect backups across your entire Organization. The key is to protect that Backup account. If you use SSO, as a minimum use a different group (or linked identity provider group) to provide access to the backup account. Ideally, you should consider a second set of credentials for access into that account.
If you want to understand more about protecting your data and backups, please get in contact with us at RedBear.