Yes, we are more than halfway through an on-point crazy re:Invent. Let’s cover the key AWS re:Invent 2023 security announcements, taking a first look at new services and features announcements. We’ve still got 2 more days to go but here’s the ones that caught our attention.
Amazon GuardDuty runtime protection
What is it?
The first of our favourite re:Invent 2023 security announcements covers new capabilities for our trusty friend, GuardDuty, AWS’s threat detection service.
GuardDuty introduced runtime threat detection for EKS earlier this year. It has now added runtime support for ECS and EC2. GuardDuty ECS Runtime Monitoring helps detect runtime events such as privilege escalation, file access, process execution, and network connections that might indicate a runtime threat. Similarly for EC2, it provides on host OS level activity monitoring, such as anomalous activity or network connections.
Why should I care?
Having insights into the runtime behaviour of compute (GuardDuty now covers runtime for EKS, ECS and EC2) provides a more 360 view of potential threats to your workloads, reducing risk for your applications and your data.
How can I use it?
It’s available today in the GuardDuty console under a new Runtime Monitoring section. Go to your delegated GuardDuty master console. There you can enable it for all accounts. Currently it only supports ECS Fargate. You can choose to manually or automatically manage the agent (a sidecar to your task).
For EC2 runtime monitoring, Amazon Linux 2 and 2023 are supported, running the 5.x or 6.x kernel versions. You also need to install a new plugin to SSM for EC2 instances.
AWS Backup automated restore testing
What is it?
When it comes to data protection, backups (or more importantly restores) are one of your friends. After all, your last backup is only as good as you last restore. In the event of a ransomware event, can you restore all your data from backups? Testing is the only way to be sure and it’s often a lengthy process. How do you known you’ve restored all the components in a workload? Enter automated restore testing and validation for AWS Backup. It’s makes it faster and cheaper to validate your recovery process.
Why should I care?
How often do you actually perform restore testing? How easy is it to produce test results for compliance? With this new feature you can validate your RTO goals and automate the process of delivering test results. You can easily catch any issues, validate your process and avoid hidden speed bumps.
How can I use it?
It’s a few simple steps to get started. There’s a new Restore testing section in the AWS Backup console. From there, you set up a Restore testing plan and define the frequency of the testing. You can then add resources (based on recovery points you already have for backed up resources). You can use tags to refine the choice. We always recommend tagging resources that are a dependent part of a workload. You can use this tag to make sure you capture all resources in the recovery testing plan.
Once restore testing has run, you will be able to see the results in the console.
AWS IAM Access Analyzer in your pipeline?
What is it?
IAM Access Analyzer has added a new feature where it can now provide custom policy checks. These checks validate that an IAM policy aligns to your security standard before the policy is deployed. Custom policy checks use automated reasoning to help detect non-compliant changes to policies. You can use these checks to automate the enforcement of policy.
Why should I care?
Allow your teams to deploy faster and safer by applying your policy enforcement at deployment time. Using this in your pipelines, you will be able to detect potential misconfigurations before they are deployed to your AWS environments. By integrating these checks as gates in your pipeline, you can avoid overly permissive policies being created in your environments.
How can I use it?
There are new API commands that you can use to test your policies defined in infrastructure as code. To use them, you need to define your reference policies (“this is what good look like”). You can then use the API to test your new policy to see if it does or doesn’t allow more access. It’s a simple idea that can be very powerful. The ever smart Matt Luttrell from AWS has put together some sample reference policies for you to try out!
Amazon Inspector agentless vulnerability assessment
What is it?
Amazon Inspector is a service that automates security assessment of EC2 instances. The service scans for unintended network exposure, software vulnerabilities, and deviations from application security best practice. It has been in the AWS portfolio since 2015 and was relaunched 2 years ago with a far more capable version. This v2 release includes support for all compute types – EC2, containers and serverless.
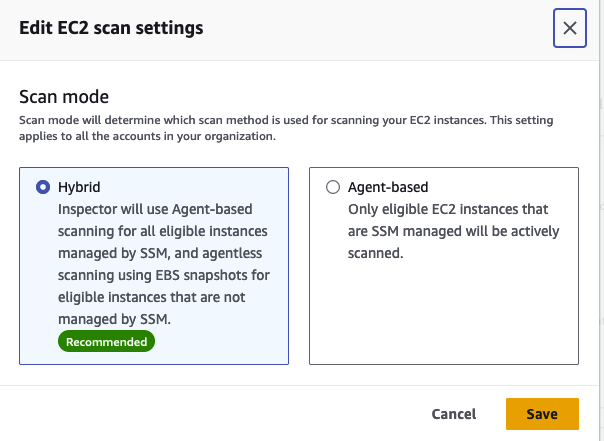
But what if you have some EC2 instances where you can’t or don’t want to install the SSM agent? Enter agentless vulnerability assessment for Inspector. With this new capability, Inspector takes a snapshot of the EBS volumes associated with the instance and scans the software for known vulnerabilities. Neat!
Why should I care?
Having an complete software bill of materials (SBOM) helps you understand your risks. You should aim to have as full coverage as possible for your vulnerability assessment program. The addition of agentless scanning means even your appliances and other instances where you can’t install an agent can now be scanned.
How can I use it?
This new capability is in preview today in a few regions. It’s super easy to enable. Just update your EC2 scan settings to Hybrid in the Inspector console. By doing so, any instance without an agent will use this scanning method. The rest will continue as they are today.
AWS Control Tower controls for digital sovereignty
What is it?
AWS Control Tower was launched in 2019 as a simple way to setup and govern a multi-account AWS environment. The idea behind it was to implement best practice through a standard set of guardrails which are applied to all accounts. At re:Invent this week, AWS announced a set of 65 controls targeted specifically at ensuring digital sovereignty for your workloads.
Digital sovereignty is all about controlling your data – where it is, where it goes and who can access or manipulate it. It can encompass geographic or access or cyptographic requirements.
Why should I care?
Knowing where you data is, who has access to it and how it is being moved and used is critical to protecting it. Data controls vary wildly for different types of data but if it is simple to apply the highest level of control to all (non-public) data, why wouldn’t you. Having a centralised place to manage those controls means that mistakes can be prevented before they occur.
How can I use it?
These new controls are available in the Control Tower console today. Find the Digital Sovereignty group of controls under the controls library. Review the controls (or have a look at the details in the Control Tower documentation).
When you are ready, you can apply the controls to an OU and all the magic (in the guise of SCPs!) will happen in the background. That’s it! We recommend applying them to a non-production OU first to avoid any unintended consequences of the new controls.
Wrapping up
What do you think of these AWS re:Invent 2023 security announcements? Do you have some other favourites? Share you thoughts with us on LinkedIn
If you want to know more about these and other announcements from re:Invent, contact us at RedBear!