re:Inforce is AWS’s security focussed conference, offering 2 days of in depth discussion on all things Cloud security. It’s a super interesting and exciting event stacked full of some great talks, ideas and inspiring stories. We found the keynote from Philadelphia particularly engaging this year. As always, it came with some interesting announcements. Let’s dive into the themes and a couple of announcements from re:Inforce 2024.
Security culture
The driving force of this year’s keynote was how to built, support and evolve your security culture. Chris Betz, AWS CISO, emphasized how AWS has been building a strong security culture since AWS’s early years. When you are managing a billion transactions a second, security cannot be an afterthought.
Some of the key points he covered that we can all learn from included
- You don’t build a culture of security overnight. Similarly, it’s not a one time activity. Rather it needs continuous feeding and watering. Much like defending against the threat landscape, if you aren’t moving forward, you actually going backwards.
- Embed security into you teams. It’s not a case of the “security team” and everyone else. AWS uses Security Guardians embedded into service teams to quickly make security decisions.
- “If you see something, say something”. Encourage escalation for security issues. It’s everyone’s problem.
- Your security technology should support your security culture but it doesn’t and shouldn’t replace it. Tools change, culture can last a generation.
AI…
Of course, no tech conference is complete without AI being front and centre. At re:Inforce 2024, there was no exception. Whether we like it or not, AI is going to change our worlds. In the security realm, it’s going to open up a whole new realm of challenges and opportunities.
The focus in the keynote was on protection of the AI models and the data within them. How do you ensure that your data remains private? How do you protect against unintentionally revealing information you should not? AWS shared details on how the underlying Gravitron and Nitro hardware platforms have been designed to isolate and protect data. It emphasized that even Amazon staff have no way to access the data within models.
This is an interesting and intentional decision to talk about how AWS supports not only its own AI based services but also AI services that it’s customers are running in AWS. It’s an area where we believe that AWS should invest more time in telling their story better. After all, they know how to securely run infrastructure at massive scale better than anyone else on the planet! We understand the desire to be higher up the stack and be the “gen AI” service provider. However, there’s a real competitive advantage to being the defacto Cloud platform for customers to run their own AI solutions.
Malware scanning for Amazon S3
Amazon S3 is one of the original AWS services. Today it’s used by almost every AWS customer and holds trillions of objects. It’s a common data store for many digital applications for content, including generated and uploaded content. One of the challenges is how do you ensure that malicious content is not uploaded to your applications. Before today, you had to build your own solution using open source or purchase a commercial offering.
At re:Inforce 2024, AWS announced an extension to Amazon GuardDuty to provide malware scanning for objects in S3. It’s really easy to enable and it will scan all new objects as they are uploaded. The integration to GuardDuty means that you can get notified of any potentially malicious content through an existing notification channel.
Let’s try it out.
To enable it, select the new Malware Protection for S3 option.
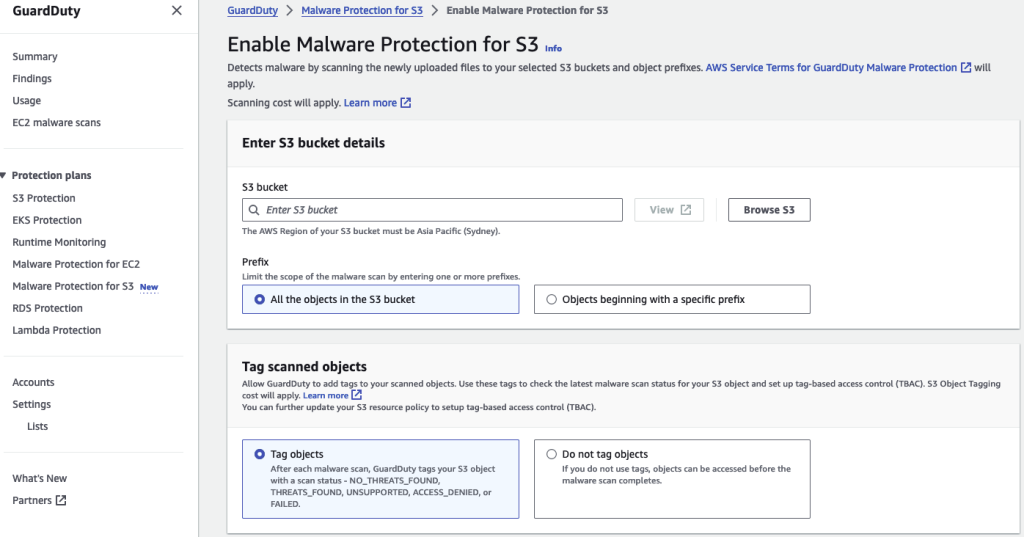
It’s enabled at a bucket level. You need to provide a role that GuardDuty can use to perform the scanning. If the target bucket is also encrypted using a KMS key, the role will also need access to use that key to decrypt the objects. You can also allow the malware scan to add tags to the buckets with the scan status. Your application can then use the tag (or an EventBridge notification) to determine if an object with malicious content has been uploaded and take action.
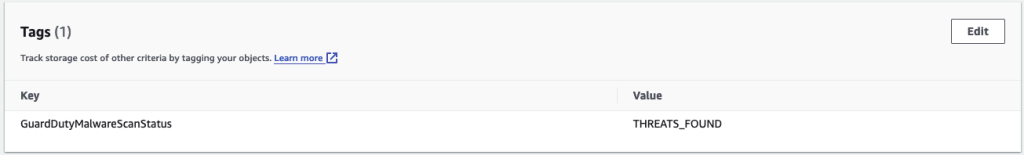
Let’s see it in action. We’ve enabled it for a bucket and uploaded an EICAR test file to the bucket. Within a minute the object is scanned. We can see the scan status tag added to the object.
The alert also appears in the GuardDuty console (and a notification has been sent to our MSSP Operations team – it’s ok, I got this, team!).
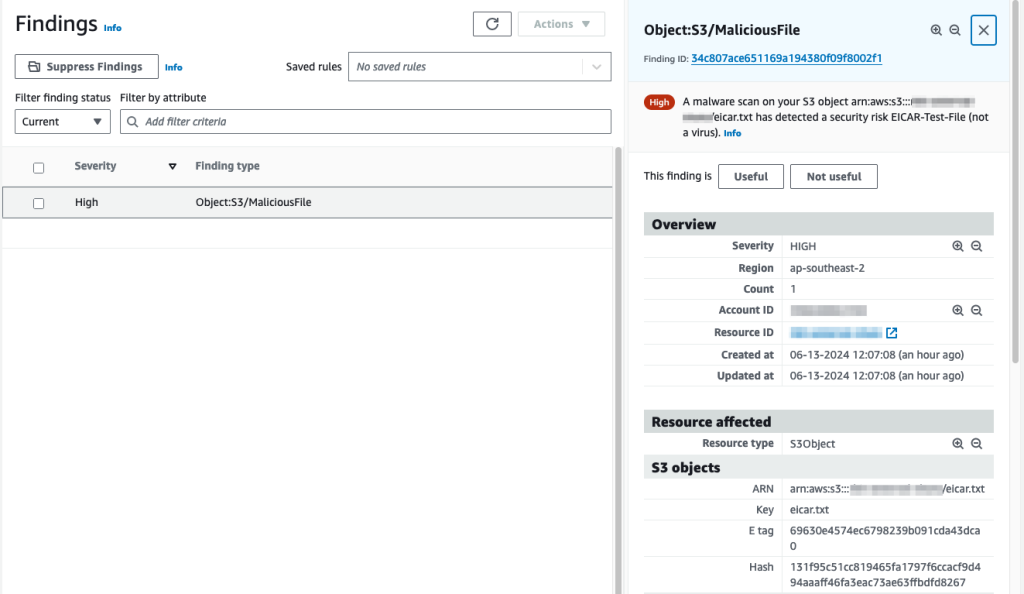
It’s that simple. Nicely done, AWS!
Curated solutions for least privileged access
Setting up least privileged access to your AWS environments for users and services is hard. Ideally, we should all look to be continuously reducing permissions. AWS IAM Access Analyzer is a fantastic tool to show what permissions are actually being used for a specific role or user. However, it’s then up to the end user to write a new policy that reflects the new reduced permission set.
Today, AWS has updated IAM Access Analyzer with some new features that will help!
- First up we have new policy checks that cover public access to resources and confirming access is not being granted to a specific resource. These help test the intention of a policy.
- The second one looks for unused access for roles and users. It will flag any unused actions within a policy or any unused resources, such as IAM access keys. However, if your problem is what to do next, then the new recommendation feature will really help you. That may be deleting an unused access key or it may be updating the IAM policy. This new feature will even provide a policy recommendation.
Here’s an example finding with unused access.

IAM Access Analyzer shows the following recommended policy.

You could now take this new policy and update your repo (because you are doing infrastructure as code, right?) to push out a new reduced level of access for the role.
Wrapping up re:Inforce 2024
What a barnstorming first day at re:Inforce. I’m sure there will be more to digest from day 2 and in the coming weeks.
If you want to know more about these and other announcements from re:Inforce 2024, or for Cloud Security in general, contact us at RedBear!


