AWS Backup has been an essential tool for protecting non-reproducible data in AWS accounts for many years. Recently, the ability to perform “logically” air-gapped backups was added. This new capability allows you to automatically copy backups to an air-gapped vault in a different account. This is an extension of the ability to copy backups between vaults that was added a few years ago.
Backups in this new vault are locked for a defined time so that neither the backup or the vault can be deleted until the hold time expires. You can also use RAM to then share this vault to a recovery account for easy restoration in the event of a disaster or ransomware event.
I’ve been testing this and thought that I would share 3 things that you need to know before you consider it or give it a try.
No support for RDS
Oops, if you want to protect your RDS databases, support is not currently provided unless they are Aurora. I assume that this is on the roadmap. However, right now this is likely to be a showstopper for alot of organizations. Your RDS databases are likely to be one of the key data stores you want to protect from ransomware events!
Amazon or customer managed keys
Are you using Amazon or customer managed KMS keys for the encryption of your resources? You are encrypting the resources you want to protect, right? Right? If not, stop reading and turn it on right now. It’s almost free and has no performance impact!
If you are using Amazon managed KMS keys, only a subset of resource types (known as resources full managed by AWS Backup) can be copied to an air-gapped backups enabled vault due to the inability to modify the key policy. Today these resources cannot be copied without re-encrypting them first within the account, before then copying to the air-gapped vault. It’s a bit of an unnecessary workaround (plus the additional cost) in my book. Alternatively, re-encrypt the source resources. Again, that’s a maintenance burden you might not enjoy. At least it is a once off activity.
However, it did reveal to me that encryption isn’t handled the way I thought it was with AWS Backup vaults. For the fully managed resources (such as S3, EFS and DynamoDB), backups use the KMS key associated with the vault. This is also true for unencrypted resources. Other resources (such as EBS or Aurora) use the same key that is used for its encryption. Yes, the backup in the vault it not encrypted with the vault key – go have a look at the protected resources in your AWS Backup vault. This was news to me. It explains why the use of an Amazon managed key is problematic when it comes to copying the backup to another vault.
I’d like to see this changed so that all backups use the vault key for encryption. It solves this problem. It also simplifies key policy management as you don’t need to allow access from the backup account.
“Logically” air-gapped backups
The key is in the detail, kids!
When I first read about this and the ability to restore backups across Organization, I really thought it was going to allow me to retire RedBear’s custom solution. Alas no.
I first setup a new air-gapped vault in an account outside of the Organization of the source vault. Then I went to test the copy between vaults, and, oops, it didn’t work!
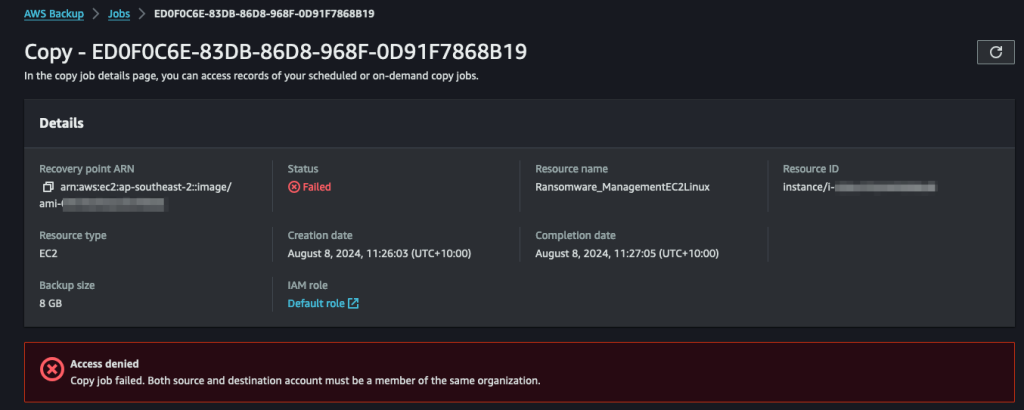
It turns out both vaults need to be in the same AWS Organization. This was not my idea of an air-gapped backup vault. Technically it is “logically” air-gapped. In the event of a compromised identity which has access to all the accounts in your Organization, they would have access to both the source and the air-gapped vault. Being able to copy backups outside of the Organization (i.e. into an account with separate authentication) is what I call air-gapped backups!
Except, of course, you can’t delete the backup as the backups in the vault are locked.
Similarly, you can’t delete the vault as there are still backups in there.

Turns out, you can delete the account though!

Now, of course, should the worst happen and someone deleted your accounts, you can contact support and recover the account within 90 days. In the panic of such a scenario, its another step to recovery. Please just let me copy to a vault in any Organization! I do like that you can at least share the air-gapped vault to any account in any Organization for recovery.
Wrapping up
Overall, I feel a little disappointed. At RedBear we have our own solution which gets around these problems and provides air-gapped backups. I really wanted to retire it. Unfortunately, today is not that day.
If you want to know more about ransomware protection, or Cloud Security in general, contact us at RedBear!


