There’s a hole in my bucket, dear Liza…
Recently, there have been a number of high profile leakages of data as a result of customer configuration of AWS S3 buckets. Let’s be clear here, this is not a problem with the AWS S3 platform. Potentially sensitive data is being stored in S3 buckets that have been set up as publicly available. It’s the kind of headline you don’t want, especially if you are a Financial Services organisation! It highlights the deal you enter in relation to your organisation’s data and Cloud Security.
Security of the AWS platform is a shared responsibility. AWS is responsible for the security of the Cloud platform. As a consumer of the platform, you are responsible for the workloads and the data you place on the platform. The beauty and power of the AWS platform is the flexibility it provides to easily, quickly and cheaply deliver new services to your business. It’s a double edged sword, though. It’s also very easy to do that in a insecure manner if you aren’t careful or knowledgable enough to understand what it all means.
“Don’t think Cloud Security is set and forget.”
AWS provides a whole bunch of tools to secure your data and to help you identify whether that is true or not in real time. At RedBear IT, we believe in providing as much visibility as possible into the security of your AWS solution. We use the AWS tools and Sumologic as part of our managed service to provide our customers with a realtime view of their security compliance posture. It’s not much knowing how secure you were 12 months ago during your last audit if you don’t have that information at your fingertips right now!
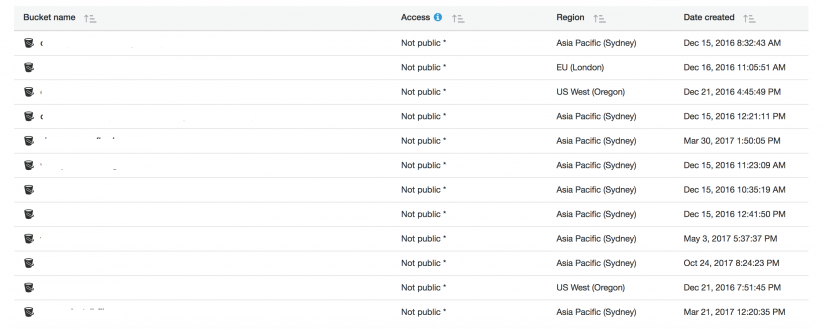
AWS have been very public in advising their customers to review their use of publicly accessible S3 buckets. They have recently updated the AWS console for S3 to show whether buckets are publicly accessible or not, a very useful and quick reference check. You should really consider and question whether you really need that bucket to be publicly accessible?
Ultimately, the workloads you run and the data you store are only as safe as you make them.
- There’s nothing wrong with using the AWS cloud to quickly spin up some workloads. In fact, it’s one of the reasons we help our customers adopt the platform. Just make sure you think about security when you do it;
- Don’t think of Cloud Security as a set and forget. You need to constantly evolve and adapt it to your business and the threat landscape;
- Use the tools that AWS provide – Macie is a fantastic way to scan your S3 buckets for potentially sensitive data;
- Ensure that you have the ability to view your security posture in (almost) realtime.
Don’t be afraid of the public Cloud. Ultimately, the AWS platform is likely to be more secure that any on-premises solution. Get building but make sure that you always consider your Cloud Security.